Linux下防御/减轻DDOS攻击工具DDoS deflate安装配置教程
#编程技术 2022-05-18 14:01:00 | 全文 2315 字,阅读约需 5 分钟 | 加载中... 次浏览👋 相关阅读
- 如何定位Mysql中CPU占用高的查询语句
- Linux系统VI方向键、删除键按出来是字母解决方法
- 树莓派开启Samba共享(smb)
- 部署 Monit 来监控服务
- 据传宝塔面板后台会上传服务器上运行的网站信息
大家都知道互联网上被 DDOS,CC 是家常便饭,在没有硬防的情况下,寻找软件代替是最直接的方法,比如用 iptables,但是 iptables 不能自动屏蔽,只能手动屏蔽,今天给大家介绍的就是一款可以自动屏蔽 DDOS,CC,SYN 攻击的软件:DDoS Deflate
DDoS deflate 官方地址:http://deflate.medialayer.com/

DOS DEFLATE 是一个轻量级的 bash shell 脚本,以协助用户阻止小规模 DDOS 攻击,它利用服务器命令创建一个连接到服务器的 IP 地址列表,以及与他们连接总数。它是在软件层面上的简单和最容易安装的解决方案之一。
DDoS Deflate 的主要功能与配置
1、可以设置IP白名单,在 /usr/local/ddos/ignore.ip.list 中设置即可;
2、主要配置文件位于 /usr/local/ddos/ddos.conf,打开此文件,根据提示进行简单的编辑即可;
3、DDoS Deflate 可以在阻止某一 IP 后,隔一段预置的时候自动对其解封;
4、可以在配置文件中设置多长时间检查一次网络连接情况;
5、当阻止 IP 后,可以设置 Email 提醒
注意:重启机器拦截的 IP 将会消失
如何查看是否被攻击
在 VPS 中输入下面的命令查看:
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
执行后,将会显示服务器上所有链接的 IP 和每个 IP 多少个连接数。
以下是我自己用 VPS 测试的结果:
[root@**** ~]## netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
1 123.207.216.159
1 162.158.170.91
1 162.55.144.211
1 172.69.33.153
1 172.69.34.8
1 172.70.142.39
1 172.70.189.36
1 172.70.210.119
1 172.70.92.253
1 172.70.93.30
1 49.204.160.110
1 Address
1 servers)
2 111.199.185.3
2 1.194.15.26
2 172.68.110.149
2 172.69.33.193
2 172.69.70.71
2 172.70.210.117
2 42.157.129.124
2 42.157.129.47
3 172.70.114.63
8 127.0.0.1
53 162.219.124.193
[root@**** ~]#
每个 IP 几个、十几个或几十个连接数都还算比较正常,如果是成百上千肯定就不正常了。
安装 DDoS Deflate
// 下载DDoS Deflate
wget http://www.inetbase.com/scripts/ddos/install.sh
// 添加权限
chmod 0700 install.sh
// 执行安装脚本
// 安装完成后会有一段版权提示与说明,按q键退出即可。
./install.sh
// 执行完删除脚本
rm -f install.sh
配置 DDoS Deflate
DDoS Deflate 的默认配置位于 /usr/local/ddos/ddos.conf,可根据给默认配置文件加上的注释提示内容,修改配置文件。
内容如下:
###### Paths of the script and other files
PROGDIR="/usr/local/ddos"
PROG="/usr/local/ddos/ddos.sh"
###### //IP地址白名单
IGNORE_IP_LIST="/usr/local/ddos/ignore.ip.list"
###### //定时执行程序
CRON="/etc/cron.d/ddos.cron"
APF="/etc/apf/apf"
IPT="/sbin/iptables"
###### frequency in minutes for running the script
###### Caution: Every time this setting is changed, run the script with --cron
###### option so that the new frequency takes effect
###### //检查时间间隔,默认1分钟
FREQ=1
###### How many connections define a bad IP? Indicate that below.
###### //最大连接数,超过这个数IP就会被屏蔽,一般默认即可
NO_OF_CONNECTIONS=50
###### APF_BAN=1 (Make sure your APF version is atleast 0.96)
###### APF_BAN=0 (Uses iptables for banning ips instead of APF)
###### //使用APF还是iptables。推荐使用iptables,将APF_BAN的值改为0即可。
APF_BAN=0
###### KILL=0 (Bad IPs are'nt banned, good for interactive execution of script)
###### KILL=1 (Recommended setting)
###### //是否屏蔽IP,默认即可
KILL=1
###### An email is sent to the following address when an IP is banned.
###### Blank would suppress sending of mails
###### //当IP被屏蔽时给指定邮箱发送邮件,推荐使用,换成自己的邮箱即可
EMAIL_TO="root"
###### Number of seconds the banned ip should remain in blacklist.
###### //禁用IP时间,默认600秒,可根据情况调整,86400 为一天
BAN_PERIOD=86400
最后将 /usr/local/ddos/ddos.sh 文件的第 117 行
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nr > $BAD_IP_LIST
修改为以下代码即可!
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sed -n '/[0-9]/p' | sort | uniq -c | sort -nr > $BAD_IP_LIST
喜欢折腾的可以用 Web 压力测试软件测试一下效果,相信 DDoS Deflate 还是能给你的 VPS 或服务器抵御一部分 DDOS 攻击,给你的网站更多的保护。
如果想看到运行日志,在 /usr/local/ddos/ddos.sh 文件的 TMP_PREFIX='/tmp/ddos' 这一行上边添加
echo -e `date '+%Y-%m-%d %H:%M:%S %A'`
并且将 /usr/local/ddos/ddos.sh 文件中 add_to_cron() 函数中的
echo "0-59/$FREQ * * * * root /usr/local/ddos/ddos.sh >/dev/null 2>&1" >> $CRON
修改为
echo "0-59/$FREQ * * * * root /usr/local/ddos/ddos.sh >/usr/local/ddos/ddos.log 2>&1" >> $CRON
/usr/local/ddos/ddos.log 为日志路径,可自定义
报错及解决
安装完成后发现没有定时任务,分析安装脚本可以看出,是执行 /usr/local/ddos/ddos.sh --cron 这一语句时报错了,错误如下:
[root@admired-poke-5 ~]## /usr/local/ddos/ddos.sh --cron
Redirecting to /bin/systemctl restart crond.service
: integer expression expected 73: [: 1
- 1)")syntax error: invalid arithmetic operator (error token is "
+ 1")syntax error: invalid arithmetic operator (error token is "
Redirecting to /bin/systemctl restart crond.service
原因是配置文件中有几个变量应该是整型,但是 ddos.conf 文件不能将配置文件里的变量识别为整形,导致变量大小判断时报错了。
临时解决方法: 将配置文件中的内容清空,直接添加配置到 ddos.sh 中
修改后的 ddos.sh 文件:
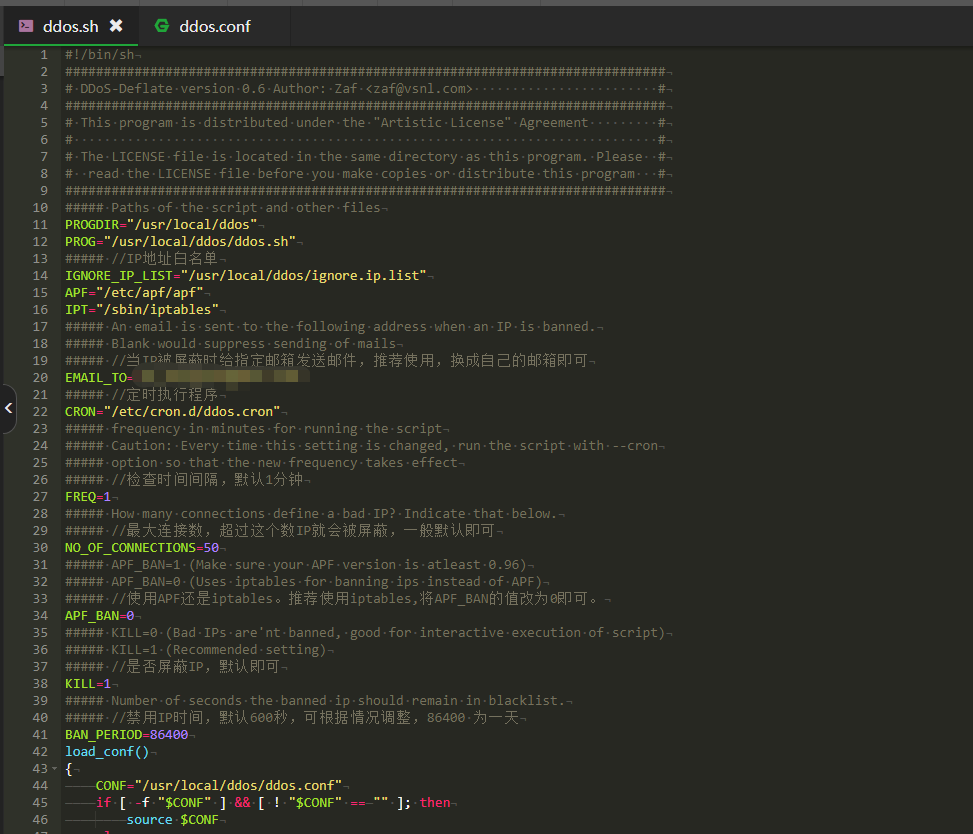
自用配置文件
优化后完整的 /usr/local/ddos/ddos.sh 文件如下:
#!/bin/sh
##############################################################################
## DDoS-Deflate version 0.6 Author: Zaf <zaf@vsnl.com> #
##############################################################################
## This program is distributed under the "Artistic License" Agreement #
## #
## The LICENSE file is located in the same directory as this program. Please #
## read the LICENSE file before you make copies or distribute this program #
##############################################################################
###### Paths of the script and other files
PROGDIR="/usr/local/ddos"
PROG="/usr/local/ddos/ddos.sh"
###### //IP地址白名单
IGNORE_IP_LIST="/usr/local/ddos/ignore.ip.list"
APF="/etc/apf/apf"
IPT="/sbin/iptables"
###### An email is sent to the following address when an IP is banned.
###### Blank would suppress sending of mails
###### //当IP被屏蔽时给指定邮箱发送邮件,推荐使用,换成自己的邮箱即可
EMAIL_TO="root"
###### //定时执行程序
CRON="/etc/cron.d/ddos.cron"
###### frequency in minutes for running the script
###### Caution: Every time this setting is changed, run the script with --cron
###### option so that the new frequency takes effect
###### //检查时间间隔,默认1分钟
FREQ=1
###### How many connections define a bad IP? Indicate that below.
###### //最大连接数,超过这个数IP就会被屏蔽,一般默认即可
NO_OF_CONNECTIONS=50
###### APF_BAN=1 (Make sure your APF version is atleast 0.96)
###### APF_BAN=0 (Uses iptables for banning ips instead of APF)
###### //使用APF还是iptables。推荐使用iptables,将APF_BAN的值改为0即可。
APF_BAN=0
###### KILL=0 (Bad IPs are'nt banned, good for interactive execution of script)
###### KILL=1 (Recommended setting)
###### //是否屏蔽IP,默认即可
KILL=1
###### Number of seconds the banned ip should remain in blacklist.
###### //禁用IP时间,默认600秒,可根据情况调整,86400 为一天
BAN_PERIOD=86400
load_conf()
{
CONF="/usr/local/ddos/ddos.conf"
if [ -f "$CONF" ] && [ ! "$CONF" == "" ]; then
source $CONF
else
head
echo "\$CONF not found."
exit 1
fi
}
head()
{
echo "DDoS-Deflate version 0.6"
echo "Copyright (C) 2005, Zaf <zaf@vsnl.com>"
echo
}
showhelp()
{
head
echo 'Usage: ddos.sh [OPTIONS] [N]'
echo 'N : number of tcp/udp connections (default 150)'
echo 'OPTIONS:'
echo '-h | --help: Show this help screen'
echo '-c | --cron: Create cron job to run this script regularly (default 1 mins)'
echo '-k | --kill: Block the offending ip making more than N connections'
}
unbanip()
{
UNBAN_SCRIPT=`mktemp /tmp/unban.XXXXXXXX`
TMP_FILE=`mktemp /tmp/unban.XXXXXXXX`
UNBAN_IP_LIST=`mktemp /tmp/unban.XXXXXXXX`
echo '#!/bin/sh' > $UNBAN_SCRIPT
echo "sleep $BAN_PERIOD" >> $UNBAN_SCRIPT
if [ $APF_BAN -eq 1 ]; then
while read line; do
echo "$APF -u $line" >> $UNBAN_SCRIPT
echo $line >> $UNBAN_IP_LIST
done < $BANNED_IP_LIST
else
while read line; do
echo "$IPT -D INPUT -s $line -j DROP" >> $UNBAN_SCRIPT
echo $line >> $UNBAN_IP_LIST
done < $BANNED_IP_LIST
fi
echo "grep -v --file=$UNBAN_IP_LIST $IGNORE_IP_LIST > $TMP_FILE" >> $UNBAN_SCRIPT
echo "mv $TMP_FILE $IGNORE_IP_LIST" >> $UNBAN_SCRIPT
echo "rm -f $UNBAN_SCRIPT" >> $UNBAN_SCRIPT
echo "rm -f $UNBAN_IP_LIST" >> $UNBAN_SCRIPT
echo "rm -f $TMP_FILE" >> $UNBAN_SCRIPT
. $UNBAN_SCRIPT &
}
add_to_cron()
{
rm -f $CRON
sleep 1
service crond restart
sleep 1
echo "SHELL=/bin/sh" > $CRON
if [ $FREQ -le 2 ]; then
echo "0-59/$FREQ * * * * root /usr/local/ddos/ddos.sh >/usr/local/ddos/ddos.log 2>&1" >> $CRON
else
let "START_MINUTE = $RANDOM % ($FREQ - 1)"
let "START_MINUTE = $START_MINUTE + 1"
let "END_MINUTE = 60 - $FREQ + $START_MINUTE"
echo "$START_MINUTE-$END_MINUTE/$FREQ * * * * root /usr/local/ddos/ddos.sh >/dev/null 2>&1" >> $CRON
fi
service crond restart
}
load_conf
while [ $1 ]; do
case $1 in
'-h' | '--help' | '?' )
showhelp
exit
;;
'--cron' | '-c' )
add_to_cron
exit
;;
'--kill' | '-k' )
KILL=1
;;
*[0-9]* )
NO_OF_CONNECTIONS=$1
;;
* )
showhelp
exit
;;
esac
shift
done
echo -e `date '+%Y-%m-%d %H:%M:%S %A'`
TMP_PREFIX='/tmp/ddos'
TMP_FILE="mktemp $TMP_PREFIX.XXXXXXXX"
BANNED_IP_MAIL=`$TMP_FILE`
BANNED_IP_LIST=`$TMP_FILE`
echo "Banned the following ip addresses on `date`" > $BANNED_IP_MAIL
echo >> $BANNED_IP_MAIL
BAD_IP_LIST=`$TMP_FILE`
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sed -n '/[0-9]/p' | sort | uniq -c | sort -nr > $BAD_IP_LIST
cat $BAD_IP_LIST
if [ $KILL -eq 1 ]; then
IP_BAN_NOW=0
while read line; do
CURR_LINE_CONN=$(echo $line | cut -d" " -f1)
CURR_LINE_IP=$(echo $line | cut -d" " -f2)
if [ $CURR_LINE_CONN -lt $NO_OF_CONNECTIONS ]; then
break
fi
IGNORE_BAN=`grep -c $CURR_LINE_IP $IGNORE_IP_LIST`
if [ $IGNORE_BAN -ge 1 ]; then
continue
fi
IP_BAN_NOW=1
echo "$CURR_LINE_IP with $CURR_LINE_CONN connections" >> $BANNED_IP_MAIL
echo $CURR_LINE_IP >> $BANNED_IP_LIST
echo $CURR_LINE_IP >> $IGNORE_IP_LIST
if [ $APF_BAN -eq 1 ]; then
$APF -d $CURR_LINE_IP
else
$IPT -I INPUT -s $CURR_LINE_IP -j DROP
fi
done < $BAD_IP_LIST
if [ $IP_BAN_NOW -eq 1 ]; then
dt=`date`
if [ $EMAIL_TO != "" ]; then
cat $BANNED_IP_MAIL | mail -s "IP addresses banned on $dt" $EMAIL_TO
fi
unbanip
fi
fi
rm -f $TMP_PREFIX.*